Article is from 2018. Someone must have pasted the url from hacker news where the same story was dug up recently.
Is that to say that it’s no longer valid? Or just that it’s old news? The list of apps associated with the software is still pretty extensive; Google Assistant even showed up.
Well these days Android asks for more permissions so I guess it would prevent it in many cases by preventing access to the microphone for apps where you don’t want to allow it…
Android also shows an indicator when any app is accessing the microphone or camera now.
https://nvd.nist.gov/vuln/detail/CVE-2023-21083
There are probably other exploits around that as well
While these bugs happen, they are fixed very quickly, and wouldn’t be used by any marketing agency. Just keep your phone updated.
it has always asked for mic permission so no change on that front
Yeah, most people just click beyond that in a millisecond because it’s just an an annoyance between them and the needed dopamine.
I think app stores can do a whole lot more, especially with he insane amounts of money they’re earning from it (hello and fuck you, apple). They can make microphone access a special privilege that requires the developer to make a special request that gets verified on the app store before the app can be released, for example
I think a middle ground may be having that requirement for background mic usage, or usage without a specific user prompt that turns on a mic.
Lots of apps have legitimate use for the mic. Apps having legitimate use for the mic while you’re not actively using the app on screen are more limited and need stricter permissions.
I’d also like to have a hardware mic mute switch that physically disconnects the mic, so I can just keep it off unless I want it like I do with the mic and Webcam on my computer.
7 years is a long time in tech.
Google Assistant is supposed to listen for the “Hey Google” trigger word. How else do you expect to use your device hand-free.
No, 2018 wasn’t 7 years ago… No… Wait please…! :'(
It also does it completely locally, using an on-device chip. If your phone has the Google assistant on it, disable all Internet and try the wake phrase, it’ll work. Nothing else does, because it has to phone home for that, but the wake phrase handling IS on-device. Can’t even turn the flashlight on otherwise tho lol, even if you use what we used to call the power button (new name for it? Lock button?) and type what you want it bitches about internet
That’s kinda my point, though. You have the Google Assistant app for a legitimate reason, and its need to use your microphone is also equally legitimate…the problem comes in when Google says that they don’t monitor what you’re saying, or worse, they say they can’t because your phone processes it all locally. They have this giant loophole that they take advantage of here, in that while they do not keep track of what you say themselves, they embed a third party service that does. While not particularly surprising given it’s Google, that’s shady as fuck and they shouldn’t be able to say they don’t monitor just because they let their little bro Alphonso do it on their behalf and they magically get off on a technicality.
Old news. It was old news in 2018
Wasn’t there just a storey a couple days ago that apps where not doing this but taking screenshots and videos on the screen and sending that. And both iOS and Android have the microphone notification now.
I know I’m usually on the more paranoid side, but I’ve always assumed everything I do on a smartphone is potentially being monitored via camera or mics.
If the apps are just taking screenshots, or recording a few seconds of data via mic, it would be almost guaranteed that certain corrupt (and also paranoid) governments that are dismissive of privacy rights could force or bribe those apps to allow them to also access screens, mics, and cameras anyway, right?
I’m in the U.S., and especially with how glitchy my phone has suddenly become over the last few months, I’m just at the point where I just assume that’s what’s going on.
I had the same android for like 4 years without many issues, then suddenly around February it just became almost impossible to use. Weird glitchy things with the size of the tool bar at the bottom of my screen and the popup keyboard. Redirect notifications all the time for certain websites, and my VPN connection is just constantly interrupted and having to be reset.
I finally was like fuck it, this is an old phone so maybe that’s it. Brand new phone, but most of the same issues.
I use signal instead of text most of the time, and switched a lot of things to proton mail, but if someone is potentially recording your screen, does it really matter if what you’re doing is encrypted?
Which VPN provider are you using? How do you know they are not the one monitoring your phone?
Did you obtained your phone from a trusted source, such as an official seller. Some phones purchased from overseas might have “International ROM” installed by the seller, which compromises the integrity of the device.
Consider having a trusted tech friend look over your phone to see if the device has malware installed.
I use proton VPN, but no I always just get my phones from Amazon bc it’s cheap. Never was a real problem in the past, but now that the U.S. is (officially) a giant Oligopoly, probably not a wise idea.
I don’t really know any tech friends that are super in the know about that kind of thing. I have a paid Norton 360 subscription that does frequent scans for malware and says it never finds anything, but honestly wouldn’t even be surprised to learn I’m paying for a useless subscription.
The only reason I even bring that up is bc our current Governor who has always been a power hungry authoritarian boot licker renewed the Executive Order for a state of emergency for a cyber incident that our previous governor first created when the data breach happened several years ago.
When he “renewed” the order, he also slipped in a new section that granted authority to the director of one of his cabinet’s agencies, Governor’s office of Homeland Security and Emergency Preparedness (GOHSEP), to handle the emergency as he sees fit.
What’s even more concerning is that on the same day he renewed this order, he restructured GOHSEP so that it is now under the control of the state’s National Guard, gave the former director of GOHSEP a new title, and then named a member of the Guard “acting director.”
He’s been very vague about what the renewal was about, but it allegedly had something to do with updating the OMV/DMV data base for the state. Since then he has also created a hiring freeze for the state, which would seem to indicate that whoever was acting director is now indefinitely the director named in the executive order until the governor decides to lift the hiring freeze.
Even for someone not already paranoid, and without everything happening at a national level, that would all be a bit concerning right? I’m not a journalist, but I’ve been trying to get people to pay attention to it.
For some reason, no actual local journalists seem to be willing to point this out, but it’s all publicly available information.
Proton is a trusted VPN/company.
Norton on PC might be useful, but on mobile, it’s probably as good as a placebo.
Good luck with your state government. Sounds like a nightmare.
The reason no local journalist is critical of the state government is because there are no independent journalists left. Google and Meta have sucked up all the advertising dollars, so small local independent media cannot survive. The journalists have to work for mega corporations who dictate what they are allowed to write.
Yeah that is kind of a given, I just wish more people would wake up to that fact.
Every day more people ate taking notice, hopefully we can hit a critical mass within our life times
try swappa for phones, when i was looking for a new phone because the Problematic pixel 5a died after a small drop, i was comparing amazon to swappa, swappa you can negotiate a lower price from the seller, and you can filter out the "corporate sellers " because they tend to so more used phones for a higher price than it should be, and you can ask questions about the phone being sold giving you more idea what your getting into.
i used to think this as well (i have never used any facebook apps), but last night something happened that made me question it.
My wife and i were going through a chipotlane that was right next to a Popeye’s. As we were waiting i looked over to popeyes and saw some posters for their new pickle chicken stuff and asked my wife “the fuck is a pickle ‘glaze’?”
she said “i have no idea but i kinda want some fried pickles now.”
literally a few seconds later she opens instagram on her phone and is shown a video of a person making pickle brined chicken.
yes yes it could be a coincidence, but i am a lot less certain of that now.
The way I’ve heard it is that it’s not just coincidence nor microphone scanning, but just the effectiveness of targeted ads in general. You could be within wifi range of other users who are searching for pickle stuff or you yourselves have a history of pickle purchases, etc. This stuff is scary specific already.
A few years ago, I would have said you were being overly paranoid. Nowadays, I’m in the same boat.
Also, the fuck is a chipotlane?
chipotle drive through
https://nvd.nist.gov/vuln/detail/CVE-2023-21083
I guarantee you that the green privacy dot means diddly squat.
Past vulnerabilities doesn’t mean there is active mpdern vulnerabilities especially ones in widely tested operating systems that’s exploited by as many apps as people claim are listening when security researchers also regularly reverse engineer and analyze the source code of popular apps to figure out what they’re doing. You can decompile Android apps pretty easily to see what they’re doing. Some are obfuscated so it takes some effort.
Its one thing to claim there’s some a system level bypass for the icon that the NSA uses to spy on its enemies, it’s another thing to claim that it’s being exploited on a wide scale by a tech companies on different apps, iOS and Android, multiple versions/devices.
The reality is that we leak tons of info through other mediums that are easier and cheaper to collect than through microphones.
This link proves how robust the security research is and how quickly bugs like that are patched.
ok thanks, but where’s the list of these apps?
These type of articles never list the apps they’re discussing.
iOS and Android. If you have one of those people are listening.
Comments like this try to make you give up on privacy by making it look like all is lost from the get to.
They are lying, don’t believe them, there is a lot you can do to protect your privacy.
Both of these apps have device-level notifications to let you know when an app is listening. I promise they’re not. There was a service a while back that was claiming this in their advertising and it went public and their partners all scattered like flies. No one wants to be associated with that sort of thing. It’s unnecessary anyway.
Eh, you can be reasonably sure that GrapheneOS or other Android ROMs without any Google Play apps is private.
No
I used to work for a mobile advertiser, and we installed hella bloatware on phones.
This idea was floated a couple times but was deemed not very effective cause you’d have to store and process hours and hours of audio data that didn’t tell us much more than just having a week or so of GPS data, your Facebook profile, and your phone IMEI.
It’s pretty easy to see if you’re near a Popeyes and what other IMEIs are connecting to the same tower, extrapolate that to you being near your wife and you and your wife thinking about shit on the Popeyes menu.
Boom targeted ad/video for fried chicken.
The rest is general tech paranoia leading to Apophenia.
There’s no microphones or cameras, it’s just the already gigantic mountain of data anyone who uses a smartphone is constantly broadcasting getting ground through the big data machine that has been the pillar of all tech since the last recession.
you’d have to store and process hours and hours of audio data that didn’t tell us much
I mean that could be solved as simply as a local transcription service…
And do what? Sentiment analysis on the conversation you were having?
Remember semantically aware models are still fairly new and even they lack the context for a particular field of text. That’s something even the new fancy LLMs struggle with.
Unnecessary when there’s way better targeted models trained on years of data that people willingly send as part of everyday smartphone use.
tf-idf will give you the keywords you want to target ads
Sentiment analysis on the conversation you were having?
Among other things, sure. More simply, keyword analysis.
Remember semantically aware models are still fairly new and even they lack the context for a particular field of text.
All of these “models” are useless garbage but it doesn’t stop them from trying to absolutely cram them everywhere they can.
Unnecessary
None of what they do is “necessary”. They could just ask you what your relevant interests are and you could tell them, but they do it anyway. They go to great lengths for any seemingly insignificant amount of data they can get their hands on.
Also, have you ever been butt-dialed by someone? 99% of the time you can’t understand a single word, let alone enough to make any semantic sense out of.
But wouldnt it be a moot point if I restrict access to GPS for all apps?
How much of that data is from Google/Apple (e.g. Google Maps)?If you use android google grabs your GPS data regardless, you have to root and disable it.
Apple does the same thing but they didn’t have their pants occupied by third-party network’s fingers like google did until the pixel came out.
Google maps is basically a beacon for AdMob to target you nearly perfectly.
Also using “fine location” in any app grabs the nearby wifi list and sends it to Google/apple if it’s not cached.
Also most ad providers these days have made deals with major networks that let them tell what tower your IMEI pinged off of.
It’s why google tried to push android/ad IDs, way less info for the networks to advertise over, and it also put the tracking in their hands instead.
So graphene os ir a degoolged phone solves the first thing
If it’s trying to figure out if you’re watching Stranger Things it can look for when you’re stationary at home and just needs to record a few seconds at a time every few minutes. I don’t know how the fingerprinting works. It might be able to run locally and not use a ton of power. We’re talking Shazam, not full text transcription.
Here’s the thing. If you watch that, Netflix know your IP. If you’re on an Android TV box, Google will know your IP.
Odds are your phone is on the Wifi. Linked through IP. Now you get ads for Stranger Things on your phone. It doesn’t need to listen because everything is so leaky. You are linked on so many devices.
Yeah, Netflix knows I’m watching Stranger Things. But afaik they don’t sell that information. And even if they do, there’s still reason for this company to try to get it themselves for cheaper. And they know something else about you based on these crappy apps they’re embedded in. So that’s all extra data points they can cross reference and get even more data.
But… they can’t access the microphone without the user explicitly allowing
Tell that to Facebook. Shit, I’ll talk about something with my wife and see ads about it ten minutes later. Been happening for years.
I tested this with my Facebook app in 2013. Found a Spanish radio station, set my phone down next to it overnight, and for several weeks I was seeing ads exclusively in Spanish. Deleted the app the first day I saw them in Spanish, and deleted my account not long after that.
My wife still uses them after 5 years together and me pointing out all the times it’s obviously eavesdropping on us, and she’s even been creeped out by it before. Still uses it…
Unless my microphone and camera have physical switches, I will assume they are being used. Those little “your camera and microphone are off” icons in the corner of the screen don’t reassure me.
This has been tested and proven time and time again. Google and Apple give apps a method to access the mic that the OS can allow or deny. This is what the apps are supposed to use.
Facebook doesn’t use that method for passive monitoring, only for active engagement. Don’t looks like it’s working when you go the use the thing and it’s disabled but it’s still listening to you.
If you must use such a social network, never ever ever use the mobile app. Use the website or don’t use the service at all.
Did you receive the Spanish radio signal over the traditional airwaves or streaming. Was it a digital radio, as those can also be tracked.
It was a stereo from 1987.
Ye Olde Analog airwaves, no fancy digital nonsense.
That’s monitoring you and your closests’ other behavior, as well as monitoring then nudging you towards wanting certain things. The ad itself is the last nudge in that chain that tries to go “you wanted this, don’t you?” after all of the other thinking it’s making a case for your life being better with it.
my wife and I had been married for 2 years. been together for close to 10.
not once did we EVER say “Adirondack Chair”. Just never came up in conversation. we were broke as fuck and couldn’t afford something as superfluous as one of those.
One day, were driving down the road home and see one on the side of he road.
what’s that?
looks like an Adirondack Chair
Adirondack Chair? For free?
yeah, it looks broken though.
we get home go inside. I sit down to veg on my phone on the sofa. what does Amazon put in my “things you like” feed? mother fuckin Adirondack Chairs. Google news feeds? Adirondack Chairs on sale.
My wife had YouTube videos that were reviewing Adirondack Chairs.
this was ten years ago. Imagine what they’re doing now…
This is stuff they could’ve gotten from location-data, or if your wifi was on, as you drive through different peoples’ wifi connections (both seeing where you’ve been, and hooking the data from you into data of people in your area to form connections of what’s trending and what they can get you to think about)
I’m not saying they’re not mass-surveilling in the most efficient ways they can, but hot-mic while sounding frightening, is the least useful tool ever for their means, and as has already been mentioned in this thread, android auto locks out that permission now anyway, making this a bad focus in the sense that it is not over just cause they can’t get to your microphone.
It’s more likely that your wife or someone nearby was further researching the same topic you were talking about.
Facebook and other ad companies use your location, relationships, and other data they already had on you to serve you relevant ads.
At this stage, they know more about you than the government, or your wife.
I’ve read about this phenomenon in the past. Generally it’s found that due to audio processing cost and the sheer amount of other data easily gathered, there’s no reason for them to snoop with your microphone because other data is so readily available, much easier to process, store and ship.
I read about that recently as well. There is a problem though. Your phone can turn your voice into text instantly. It’s a feature built in to your keyboard. They could turn the audio into text and then transmit the text only. Saves much data that way.
Honestly these days they could process the audio on your phone with a small audio classification machine learning model, although nowadays phone os’s show if the mic is in use
Bullshit. The amount of times I’ve had random conversations about odd topics for the very first time with my wife and the fucking subject appears in a FB add three hours later.
Nope, go peddle your corpo propaganda elsewhere.
Only on iOS. Also a lot of apps can present valid uses for microphone access, which prompts users to allow unlimited malicious use
I can be absolutely certain no apps can access my mic in the background. Even when in the foreground, there is a hot-mic indicator.

Here’s the misleading part:
Tap on one of those “while in use” apps. You’ll see there is no option “allowed all the time.” It doesn’t exist.
“while in use” is top level, and changes to “while using the app” when you actually look at the permission. They really mean when the app is running. And many often run in the background.
Theoretically if mic gets accessed it should be lighting the indicator. Not sure if that’s how it actually works though.
Not only on iOS. I use Android and my microphone is always off unless I allow a specific app to use it, and even then, I have the option of only allowing it for that one time. Including the phone app.

Mic and camera are always off.
What happens when you answer the phone?
A little pop up comes up saying something about “getting the most out of your phone” with the option to turn the mic on for the app that’s requesting it (phone app). Only turns on for the call. Just gotta tap the screen once.
I keep the mic and camera options at the top of my quick-… whatever they call them… options, so if I need either one for something else, it’s super easy to turn off/on.
Android shows a little green logo in the top right if the mic and/or camera is on as well. So if I ever do enable them, it’s easy to remember to turn them off again.
Thanks I’m gonna try it out for a while
It works great for me. I’m using a Pixel with stock Android, so I can only speak to how it behaves on my phone. I know sometimes carriers add/change shit.
I did this but stopped because if I pick up the phone locked, I have to unlock it to turn mic on and answer the call. So I just make sure to allow mic access only to apps that really need it
Check out GrapheneOS
Because it is software-based access control, it is impossible to guarantee that access really has been disabled. Thanks to Apple’s design, we now live in a world where users are not supposed to detach batteries or physically turn off microphones and cameras; it’s all software-controlled. The problem is that software can be hacked and have backdoors. Also, thanks to Apple’s smart design, users can no longer upgrade the memory sticks on their Mac Minis and MacBooks. Why do I say it is all Apple’s fault? Unfortunately, other manufacturers copy these design ideas…
I thought Android has a non bypassable green dot in the notification bar when the micro is on ?
Users need to know what this dot means, and some like children or the elderly will likely not understand the ramifications
I feel like you’re missing the point. Showing a green dot still doesn’t solve the problem or make it ok, especially when this technology works in the background and can capture sound even while the device is in your pocket, like the article says.
I don’t think we should have to be on the lookout for a little dot showing up on the screen constantly. It shouldn’t even ask for microphone access unless it’s absolutely essential for the app’s main purpose. “Features” like this should always be off by default and buried deep in the settings. If people really wanted it (they don’t), they’d go in and turn it on themselves.
You’re absolutely right but that wasn’t my point. I thought that if one of my installed app was doing this, at some point I’d have seen it without even being on the lookout.
This is literally how it works. In modern android you need to explicitly grants microphone permission to apps the first time you use them. Now, if they are clickjacking the permission notification, that’s something different, but the article doesn’t mention this. You can download your own microphone logs and verify if you are curious about this.
It’s probably bypassable too. And, anytime the microphone is used, you have no idea the multiple extents that data is being used for.
Apps can use the microphone in secret and there’s no way to know when they’re using the microphone? This is a major security flaw in Android!
Are you kidding? You do know that basically anything is hackable, right? And that’s why old people put tape and stuff over their cameras if they don’t just outright unplug them, right? It seems silly, but like… They’ve always been right, with their insane passwords and avoiding using their real names and stuff.
afaik Android System Intelligence and apps using that will not show the mic icon
Right around the confinement my sister and I were talking about getting some seeds for my mom. Neither of us searched for seeds. From that point we both started to get ads for seeds, many for the ones we had talked about in particular. This thing was so unequivocal that it proved to me that our phones listen. Maybe they don’t analyze, but they definitely listen for words actionable for an advertising purposes.
That’s why i always forbid access to my microphones by apps. Many AI apps will also remember what you discussed long ago.
OS doesn’t need permissions to access hardware
More likely, your late’ish habits and searches combined with age and another mountain of data correlated with people that have the same thought. We are no snowflakes.
Edit: I should say, if this example is true. I’m not saying you are lying, just that if you are, it’s not a “gotcha”. This thread is making me paranoid! :)
The thing is you can test it, simply never search anything related to it and see if you get ads, maybe I accidentally searched something but it works, or it could be wifi based maybe they searched something and it effected everyones ads, this could make sense if my roommates searched stuff and it effected my ads
deleted by creator
Go ahead, make TVs more smart. We literally removed our TV thus weekend. If you want me to upgrade it, please removed the spyware.
My tvs are connected to an SSID that can’t hit the internet. I blocked them before but my dumb ass neighbor left their WiFi unprotected and my tvs just connected to them because it couldn’t get out the internet on my network. So I created an SSID logged them in and blocked it from the internet. It doesn’t bounce to open WiFi anymore. If I block it completely from the network the WiFi just disconnects from the network because it can’t hit anything. I have LG’s.
The fact that they just desperately jump on any network is absurd. Its acting like malware.
It’s not an act!
That is an insane thing to have to do. Having to manipulate your TV into not doing something you don’t want or require it to do.
Why is it even legal for it to just hop open networks automatically? Sure, if you leave your wifi unsecured you’re dumb and anyone can access it, but it’s still not a network you have permission to access
I don’t think it’s illegal. The TOS could just be saying “If you connect me to the internet you consent me upgrading myself.” It doesn’t say how hard it’s allowed to try to connect.
Same. The only ‘TV’ I currently own is my monitor. Fuck that shit, I’m so over modern television as a concept.
Next TV that breaks and we won’t have one. I’ll do a projector for movie night and that’s it.
I keep my phone in a chip bag and only pull it out to LARP the preparation for the assassination Franz Ferdinand in general terms without naming actual places or names.
That’s a good way to always keep chips on hand.
On the other hand, it’s amazingly easy for advertisers to figure out what topics / products you’re talking about without the need for constantly recording via your microphone. In most instances, it doesn’t even really make sense to constantly record audio via the mic to monitor folks, other means are much more cost efficient while being just as effective. That’s not to say that some app isn’t or hasn’t done it, just that historically speaking, it hasn’t been as ubiquitous as a lot of people seem to think or imply.
Sometimes with these things, you have to apply Occam’s Razor.
I stayed with some family during the holidays a few years ago and they are conspiracy theory fanatics unfortunately. The type that swear their phones are listening to everything they say. They get ads for things they’ve only ever talked about in person. That sort of thing.
As proof, they pointed out how the prior night the topic of old timey candy from our childhoods came up and all of a sudden they were getting news stories and facebook ads about those liquid filled wax bottle candies. To them, the only plausible explanation is that our phones were listening to us.
Except, as I pointed out, I specifically looked those wax bottle candies up later that night because I was curious if they were still for sale. They live way out in the country and there’s limited cellular data, so basically everybody there that night was using the same wifi connection. Which means, our internet activity is all linked because to the outside world, we’re all on the same network/IP address. Even more curious, though, nobody got ads for any of the other candy that we talked about and which I didn’t specifically look up. So, if our phones were actually recording us and serving up ads based on the things we talked about, then why didn’t we get ads for Blackjack gum, wax lips, and Brach’s? Only the very specific one I happened to search for.
This is what a lot of people don’t get. Plus often people see an ad or content and forget. Later they bring it up without realizing the thing is trending. It’s all self feeding.
So much of social media (and online in general) is just ads in disguise and people shilling products, intentionally or otherwise, and it ultimately spills over into real life conversations. So I agree with you completely.
You might have given a thumbs up to your aunt Gina’s photo of her and her friends at the office party celebrating her promotion. Ad networks see it as you interacting with a photo that contains a bottle of Schmudd soda, even if that’s a detail you didn’t even notice.
You have dinner with your dad that night and the topic of Schmudd comes up due to the latest forced controversy (ermagerd the trans) so naturally when you start seeing Schmudd commercials the next day, you might assume your phone was listening to that conversation. But actually the reason you’re seeing the ads is because of the thumbs up to aunt Gina’s post.
And yes, the tracking and analytics tools find those types of patterns and relationships, and so much more. And they’ve been able to do that for over a decade. No telling how good it’s gotten since I was last working adjacent to that field.
Good thing everyone diligently reads the T&A of Pool 3d before using it. You are reading every line of text before you hit agree, and then uninstall, right?
Use NextDNS with strong filters and the DDG app with App Tracking Protection turned on. While no filter is 100% perfect, this combo stops the vast majority of privacy-invading shit from getting to 3rd parties.
I use shizuku for hidden api/shell access…the devs of that have an app called appops which, you guessed it, allow you to change any appops permission for any app. Allows denying/ignoring clipboard access, device identifiers, location, microphone, etc.
appops screenshots


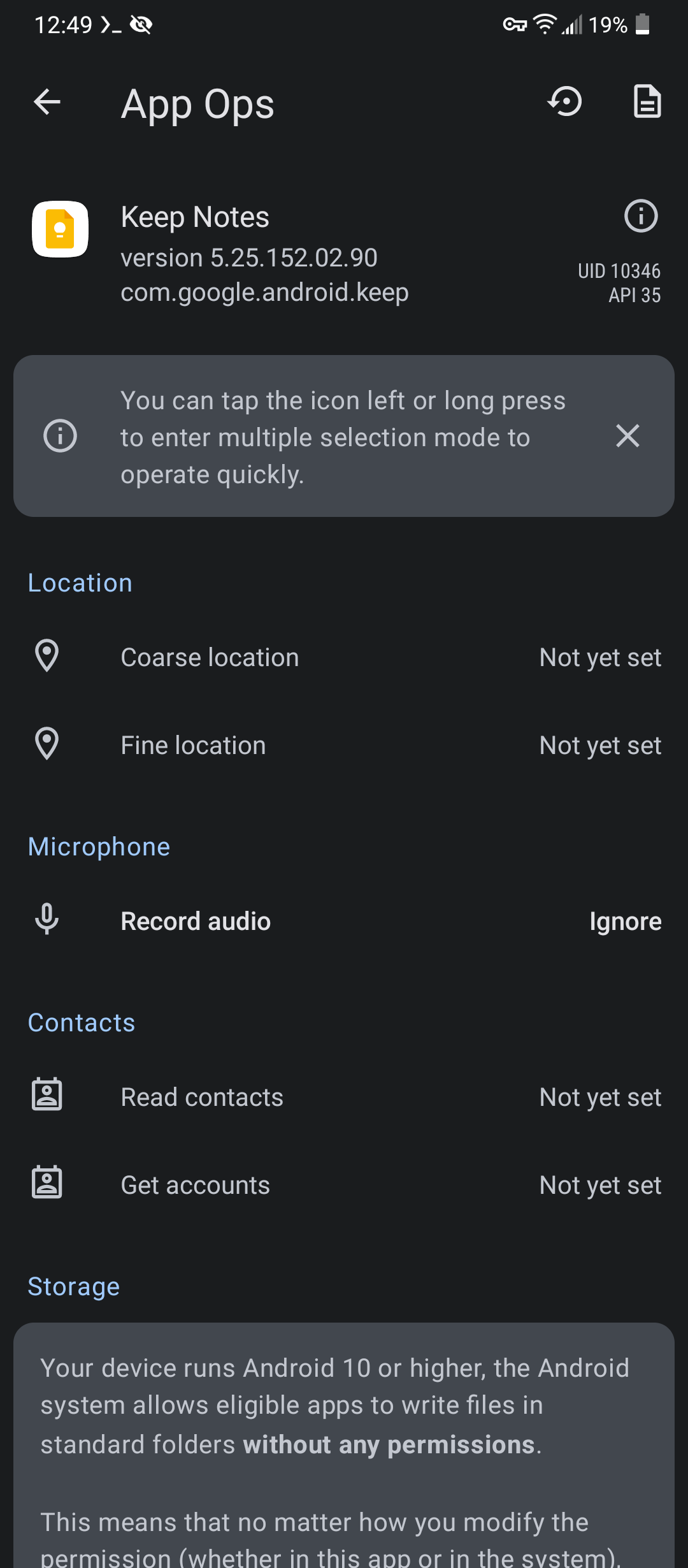 :::
:::App Ops still works? I haven’t used it in over a decade.
And people wonder why I keep rooting my Android phones.
Without advanced permission denial and file access restrictions, phones will spy on anything and anyone.
That helps with other dangers, but in this case all you need to do is not give “Pool 3D” access to the microphone, no rooting required.
Rooting is no longer required and is a security risk
Or do you mean flashing custom privacy respecting rom
No, I exactly mean rooting, and it is a hard requirement for me when choosing phones.
If you know what you’re doing, there is no security risk involved, since every app requesting for root access needs to be granted individually, and you can opt to do so for a limited time or permanently. Or not grant it at all, obviously.
Tools like AppOps (advanced permission management), Storage Isolation (prevent access to certain folders even if “file access” permission is granted to some app), Ice Box (keep certain apps in a permanent state of hibernation unless you explicitly launch them) are absolute core essentials.
Other apps that enable you to fully remove system apps, system level adblockers, VPN sharing etc. might be optional, and there are no-root workarounds, but they all come with serious limitations.
Doesnt GrapheneOS provide some of these features?
That’s only available for Pixel phones, and I don’t buy from Google.
Little nitpick: Graphene OS isn’t artificially restricted to Google phones. Pixel phones just happen to be the only ones that fulfill the safety requiremets that Graphene OS wants.
Other manufacturers could do the same and Graphene OS devs would welcome it, they just choose not to do that.
Appops is great. Just mentioned in another comment ,though I use shizuku.
Hmm… Do you use a different root method than magisk? I don’t think a root method based on the efforts of a single developer is a safe practice.
There are other tools, but their developers aren’t publicly known. So I indeed trust into the one man show that is magisk, at least as a full time Google employee who gets his codebase reviewed in-house, there’s some more trust than to a random nobody. And he does publish the code and allows for user contributed fixes on github.
Granting blanket root to all programs on an android phone sure that’s a risk; but who the fuck does that on any system…
From memory individual apps would be able to request root which could be denied, approved once, approved always or ignored.
Why would you provide any app with root access tbo?
What do they need it for?
Not OP but rooting is still necessary for advanced backups like those made using Swift Backup
Really depends on what you want to do.
Same as any Linux system you don’t want applications to have root access all the time. However if I want to remove a system file or modify something that a normal user isn’t able to, something is going to require higher privileges than the standard user account has.
This might just push my fear of targeted ads enough to give in to my idea of a nearly soundproof box for my phone when I’m not using it. :(
Just install an OS that allows per-app microphone permissions. I’m running LineageOS and I can tell it for example to only allow Whatsapp mic access when I actively open the app. Actually according to the article, the same can be done on plain Android too.
You could remove the mic and pretend it’s a modern iPod 😁
Nah, I’m not that paranoid and I need the mic for calls.
deleted by creator
About things the other person has searched for and visited and when their networks touch it spreads. It’s easy to do without a mic
















